Identifying weak implementations of
SSL/TLS
As you learned in the previous section, TLS is a combination of various encryption
algorithms packaged into one in order to provide confidentiality, integrity, and
authentication. In the first step, when two endpoints negotiate for an SSL connection, they
identify the common cipher suites supported by them. This allows SSL to support a wide
variety of devices, which may not have the hardware and software to support the newer
ciphers. Supporting older encryption algorithms has a major drawback. Most older cipher
suites are easily breakable in a reasonable amount of time by cryptanalysts using the
computing power available today.
The OpenSSL command-line tool
In order to identify the cipher suites negotiated by the remote web server, you can use the
OpenSSL command-line tool that comes preinstalled on all major Linux distributions, and it
is also included in Kali Linux. The tool can be used to test the various functions of the
OpenSSL library directly from the bash shell without writing any code. It is also used as a
troubleshooting tool
The following example uses the s_client command-line option that establishes a
connection to the remote server using SSL/TLS. The output of the command is difficult to
interpret for a newbie, but it is useful for identifying the TLS/SSL version and cipher suites
agreed upon between the server and the client:
The OpenSSL utility contains various command-line options that can be used to test the
server using specific SSL versions and cipher suites. In the following example, we are trying
to connect using TLS version 1.2 and a weak algorithm, RC4:
openssl s_client -tls1_2 -cipher 'ECDHE-RSA-AES256-SHA' -connect
<target>:<port>
You will often see cipher suites written as ECDHE-RSA-RC4-MD5. The format is broken
down into the following parts:
ECDHE: This is a key exchange algorithm
RSA: This is an authentication algorithm
RC4: This is an encryption algorithm
MD5: This is a hashing algorithm
A comprehensive list of SSL and TLS cipher suites can be found
at https://www.openssl.org/docs/apps/ciphers.html.
SSLScan
Although the OpenSSL command-line tool provides many options to test the SSL
configuration, the output of the tool is not user friendly. The tool also requires a fair amount
of knowledge about the cipher suites that you want to test.
Kali Linux comes with many tools that automate the task of identifying SSL
misconfigurations, outdated protocol versions, and weak cipher suites and hashing
algorithms. One of the tools is SSLScan, which can be accessed by going to Applications |
Information Gathering | SSL Analysis.
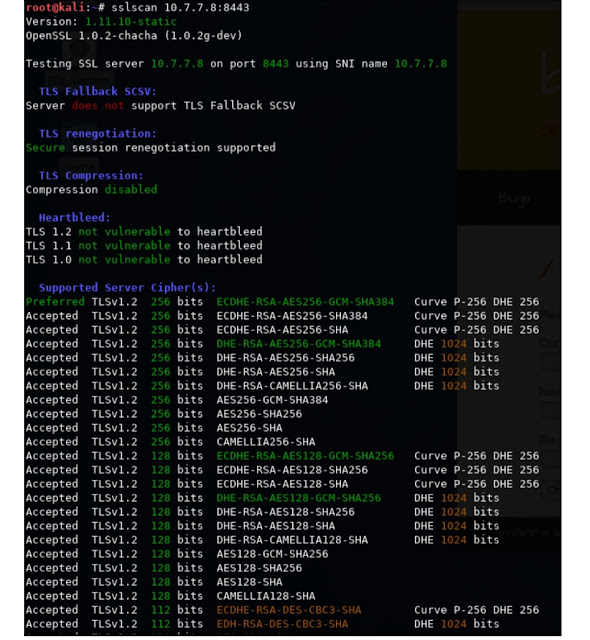
By default, SSLScan checks if the server is vulnerable to the CRIME and Heartbleed
vulnerabilities. The -tls option will force SSLScan only to test the cipher suites using the
TLS protocol. The output is distributed in various colors, with green indicating that the
cipher suite is secure and the sections that are colored in red and yellow are trying to attract
your attention:
The cipher suites supported by the client can be identified by running the following
command. It will display a long list of ciphers that are supported by the client:
sslscan -show-ciphers www.example.com:443
If you want to analyze the certificate-related data, use the following command that will
display detailed information on the certificate:
sslscan --show-certificate --no-ciphersuites www.amazon.com:443
The output of the command can be exported in an XML document using the -
xml=<filename> option.

.jpeg)


.png)
.jpeg)

.png)
.jpeg)
